It may seem silly, but it’s so difficult to find proper information about a DRM is, what it isn’t, and broadly, how it works.
What is not a DRM
Most people associate a DRM with content protection, a way to protect the content. However, stricto sensu, it isn’t.
A DRM system is not about how contents are protected or encrypted. In fact, most current DRMs use exactly the same encryption methods to protect content, and again contrary to most DRM way of thinking, these methods are public and vary between AES-CTR and AES-CBC. If you find those names too familiar, it’s because they are. AES is an industry standard developed in 1998, and used extensively throughout the whole IT infrastructure, including the way this web page is protected to bring to you this article. If you wonder if this content is worth enough to be protected by such a strong method, it’s probably not. However AES also serves other purposes, such as making sure this website is actually what you think it is, and that it’s contents were not altered, (e.g. not having malicious code) making it more relevant from a search engine perspective.
The is one exception though, live broadcasting systems often don’t use AES to encrypt the content, but a different method know as “Common Scrambling Algorithm” or CSA, currently on it’s third version. Other than that, the remaining of the workflow regarding “Conditional Systems” (as Cable Operators call it) work mostly the same way a DRM does, and exactly the same way on most modern CA systems,
Understanding what a DRM isn’t helps explaining where the DRM flaws and weaknesses are, or in this case, aren’t. There isn’t a single documented case where content was distributed because the encryption system was breached, and this is good news, as AES is what protects our home banking and most important internet resources.
Another thing that isn’t a DRM is an authentication nor authorisation systems. When you insert your login and password on Netflix, it’s Netflix’s IT and BSS systems which check that you are one you say you are, and which content you’re entitled to see. In fact, most OTT providers over there simultaneously support a number of DRM systems using the same user credentials.
Still not a DRM, but near
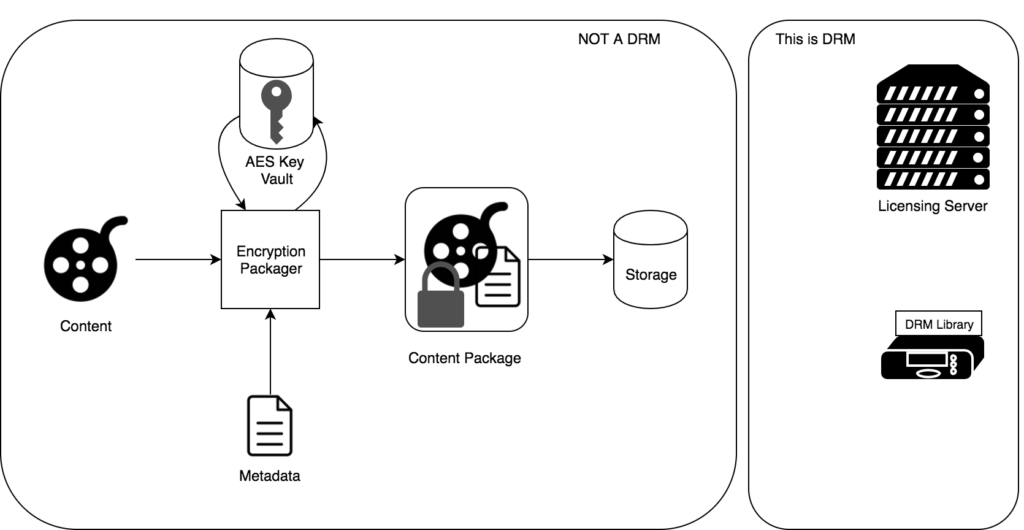
In order to use a DRM, content needs to be ingested using what is often called a Content Management System (CMS). The workflow of a modern content management system using a DRM system can then be described as follows:
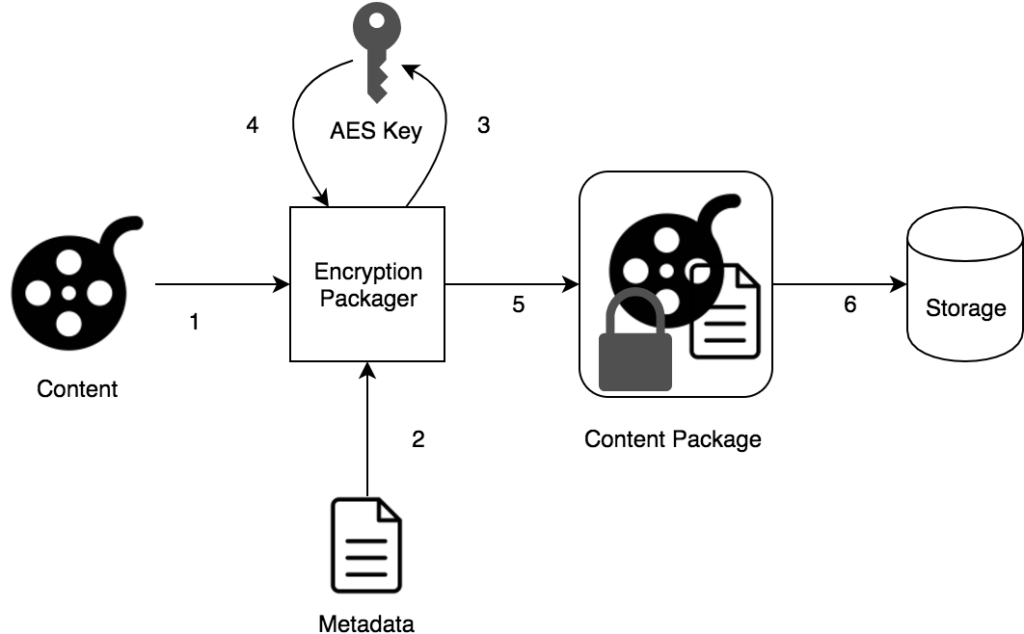 Content is sent to an encryption and packaging orchestrator.
Content is sent to an encryption and packaging orchestrator.- In parallel, a set of metadata is also sent to the packager. This metadata may contains user facing information such as cast and crew, but more important to a DRM system, the usage rules. At this point, the term “usage rules” is very broad, and may include information such as associated package, authorised devices, restricted outputs and any other information regarding where, when and how that content may be played.
- Packager requests and AES key from the Key Vault, by providing a content identifier. If different DRM systems provide the same identifier for the same content, then the same AES key will be returned. This is the core of a “Multi-DRM” system.
- Key Vault diligently returns the key associated with the provided identifier, generating one if the identifier not already associated to any key.
- With all those parameters at hand, the orchestrator encrypts the content, using the AES key obtained previously, and packages it. This package includes not only the actual video and audio, but also the associated metadata, in a format which is easily processable.
- Finally, the encrypted content is simply stored on a cheap, possible insecure, storage.
This is the way a modern content management system works, and yet, there’s no DRM involved. In fact, this underlines what a DRM system isn’t.
